Data Science Bootcamps – Building a Strong Foundation for Data-Driven Careers
In today’s data-driven world, the demand for skilled professionals in data science continues to surge. Data science bootcamps have emerged as intensive, short-term training programs designed to equip individuals with the essential skills and knowledge needed to thrive in this rapidly evolving field. These bootcamps offer a structured learning path that combines theoretical foundations with practical hands-on experience, making them an attractive option for career changers and recent graduates alike.
The Structure and Curriculum
Data science bootcamps typically span several weeks to a few months, focusing intensely on core concepts such as statistics, machine learning, programming languages like Python or R, and data manipulation techniques. The curriculum is crafted to bridge the gap between academic theory and real-world application, ensuring that participants gain proficiency in using tools and technologies that are currently in demand across industries. Participants engage in projects that simulate real-world scenarios, allowing them to apply their learning to solve practical problems. This project-based approach not only enhances technical skills but also cultivates critical thinking and problem-solving abilities essential traits for successful data scientists.

Hands-On Learning and Mentorship
One of the key advantages of data science bootcamps is the hands-on learning environment they provide. Participants work on projects individually and in teams, receiving guidance and mentorship from experienced instructors who are often industry professionals themselves. This mentorship aspect not only accelerates learning but also provides valuable insights into industry best practices and trends. Moreover, many bootcamps offer career support services, including resume building, interview preparation, and networking opportunities with potential employers.
Flexibility and Accessibility
are data science bootcamps worth it Data science bootcamps cater to a wide range of learners, from complete beginners to seasoned professionals looking to upskill. They are offered in various formats, including in-person, online, and hybrid models, making them accessible to individuals regardless of their location or schedule constraints. Online bootcamps, in particular, have gained popularity for their flexibility they allow participants to learn at their own pace and from anywhere in the world. This accessibility is crucial for those balancing work or family commitments while pursuing career advancement in data science.
Building a Strong Foundation for Career Growth
For aspiring data scientists, enrolling in a bootcamp can be a strategic career move. Beyond acquiring technical skills, participants develop a portfolio of projects that demonstrate their ability to tackle complex data problems. This portfolio serves as tangible proof of their expertise to prospective employers, helping them stand out in a competitive job market. Furthermore, the interdisciplinary nature of data science drawing from fields such as statistics, computer science, and domain-specific knowledge positions bootcamp graduates as versatile professionals capable of contributing across various industries.
Data science bootcamps play a vital role in preparing individuals for data-driven careers by providing them with a robust foundation in essential skills, practical experience through hands-on projects, and valuable industry insights. Whether you are looking to pivot into a new career or enhance your existing skill set, these bootcamps offer a structured pathway to success in the dynamic field of data science. By equipping yourself with the right tools and knowledge, you can embark on a fulfilling career journey that leverages data to drive innovation and decision-making in today’s digital landscape.
...Leveraging CI/CD Frameworks for Agile Development and Deployment
Continuous Innovation CI is a fundamental aspect of modern software development, facilitating the rapid iteration and improvement of products. This approach is particularly potent when combined with Continuous Integration/Continuous Deployment CI/CD frameworks, enabling agile development and seamless deployment processes. CI/CD frameworks streamline the development pipeline, automating various stages from code integration to deployment, ensuring a consistent and efficient workflow. At its core, CI involves developers frequently integrating their code changes into a shared repository. This practice minimizes integration issues by detecting errors early in the development cycle, promoting collaboration, and maintaining code quality. CI tools like Jenkins, Travis CI, or CircleCI automate the build and test phases, providing immediate feedback to developers. This rapid feedback loop accelerates the development process, empowering teams to iterate quickly and deliver high-quality software. CD extends CI by automating the deployment process, enabling developers to release code changes swiftly and reliably. CD pipelines orchestrate the deployment process, from packaging applications to deploying them to production environments.
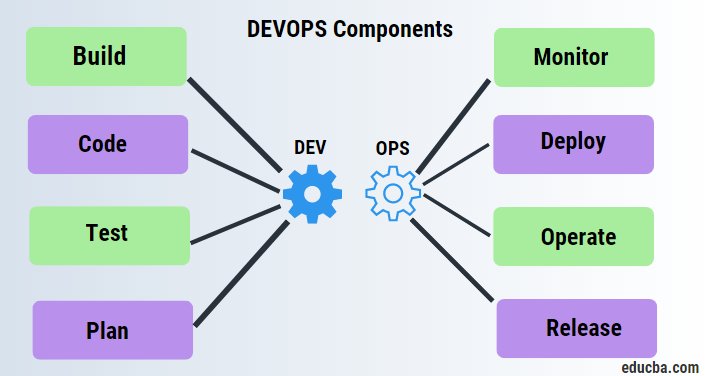
Leveraging tools like Docker and Kubernetes, CD pipelines ensure consistency between development, testing, and production environments, reducing the risk of deployment failures and enhancing the overall reliability of software releases. The synergy between CI and CD fosters agility within development teams. By automating repetitive tasks such as building, testing, and deployment, developers can focus on creating value through innovation. Agile methodologies, such as Scrum or Kanban, complement CI/CD practices by emphasizing iterative development, customer feedback, and adaptive planning. The combination of CI/CD and agile methodologies empowers teams to respond quickly to changing requirements and market dynamics, delivering solutions that align closely with customer needs. Furthermore, CI/CD frameworks promote a culture of continuous improvement within organizations. By continuously integrating and deploying code changes, teams can gather valuable feedback from users, monitor application performance, and identify areas for enhancement. This feedback loop facilitates incremental improvements, allowing organizations to adapt to evolving market demands and technological advancements swiftly. Continuous improvement becomes ingrained in the development process, driving innovation and enhancing the competitiveness of the organization.
In addition to accelerating development cycles and fostering innovation, CI/CD frameworks enhance the reliability and stability of software applications. Automated testing ensures that code changes meet quality standards before deployment, reducing the likelihood of introducing bugs or regressions into production environments and click site https://quema.co/continuous-integration-continuous-delivery. Moreover, the automated deployment process minimizes human error, leading to more consistent and predictable releases. As a result, organizations can deliver software with greater confidence, enhancing customer satisfaction and trust. However, implementing CI/CD frameworks requires careful planning and investment in infrastructure, tooling, and training. Organizations must cultivate a culture that embraces automation, collaboration, and continuous improvement to fully realize the benefits of CI/CD. Moreover, security considerations should be integrated into CI/CD pipelines to ensure the integrity and confidentiality of sensitive data. Despite these challenges, the adoption of CI/CD frameworks represents a significant opportunity for organizations to drive continuous innovation, deliver value to customers, and stay ahead in today’s fast-paced digital landscape.
...Evolution in Design and Functionality of Apple’s EarPods and AirPods
Apple’s journey in revolutionizing audio experiences began with the introduction of EarPods, the wired earphones that accompanied iPhones and iPods. Released in 2012, EarPods represented a departure from the traditional earphone design, featuring a unique shape that aimed to improve comfort and sound quality. The shift from the circular design to a more contoured, ergonomic shape marked the first step towards user-centric design, aiming to provide a better fit for a broader range of users. However, it was not until the advent of AirPods in 2016 that Apple truly redefined the wireless audio landscape. AirPods not only cut the cord but also introduced a host of innovative features, transforming the simple act of listening to music into a seamless and magical experience. The design of AirPods focused on minimalism, featuring a compact charging case that doubled as a power bank and a streamlined, stem-like structure for the earbuds. This design not only made a fashion statement but also addressed the challenge of ensuring a secure fit without compromising on aesthetics.
The evolution from EarPods to AirPods marked a pivotal moment in the wireless audio industry, setting new standards for functionality and convenience. Difference between EarPods and AirPods transition to a completely wireless design not only eliminated the nuisance of tangled wires but also introduced features like automatic ear detection and touch controls. The intelligence embedded in AirPods allowed users to experience a new level of freedom removing the earbuds automatically paused playback, and tapping the earbuds enabled users to control music playback and answer calls effortlessly. Moreover, Apple’s commitment to enhancing the user experience extended to the integration of Siri, the virtual assistant, into AirPods. Users could now perform tasks like adjusting volume, changing songs, or even getting directions by simply summoning Siri through voice commands. This hands-free approach elevated the functionality of AirPods, turning them into more than just audio accessories but intelligent personal assistants.
The evolution in design and functionality did not stop with the first generation of AirPods. Subsequent iterations introduced features like active noise cancellation ANC and spatial audio, creating an immersive audio experience. The addition of sweat and water resistance in the AirPods Pro further expanded their utility, making them suitable for workouts and outdoor activities. In conclusion, the journey from EarPods to AirPods represents a remarkable evolution in both design and functionality, showcasing Apple’s commitment to enhancing the user experience. The transition from wired to wireless not only liberated users from tangled cables but also introduced a new era of intelligent, feature-rich earbuds. As Apple continues to push the boundaries of innovation, the future of audio experiences seems destined for even greater heights, promising a harmonious blend of design elegance and technological prowess.
...Bing Ads and Ad Words a Reasonable Choice for Little Financial plan Advertisers
Is Bing Ads and Ad Words a down to earth decision for little spending plan advertisers? From my own involvement with utilizing these two Compensation For every Snap Web search tool advertising apparatuses, I would need to say, no. I have spent a sum of around 8,000 bucks consolidated to advertise over the Web utilizing Bing Ads and Ad Words PPC with no profit from my speculation at all. In view of this absence of profit from my venture, I have quit utilizing both Bing Ads and Ad Words Web advertising devices since I can’t bear to squander my pitiful financial plan on them without anything positive to show for it. I didn’t arrive at the resolution to stop utilizing Bing Ads and Ad Words PPC immediately, which I ought to have, instead I followed a portion of their ideas and changed my ads to make them look really engaging, utilized negative and long-tail watchwords, made sure that my greeting pages were legitimate, bid as high as my spending plan would permit on specific catchphrases, etc. with next to no expansion in deals nor however many hits on my website as I needed.
There are numerous Web promoting tricks that a private company ought to know for while picking a PPP administration. One method for learning about these organizations is through typical examination by seeing client audits of the organization yet remember that numerous Web organizations have their own client survey websites that are outfitted to advance them. To err on the side of caution you ought to find however many client surveys of an shopify设置必应广告 as could be expected under the circumstances, particularly the item and administration audits that have been given by genuine clients and not paid commentators.

No matter what the product(s) and administrations that an advertiser is promoting, a little advertising financial plan is no rivalry by any stretch of the imagination against organizations that can burn through large number of dollars a month on advertising and showcasing. I took in a hard example by squandering my cash going toward the enormous young men and young ladies that have a huge number of dollars dispensed exclusively for showcasing and advertising, and this is the sort of thing that a private venture should consider while choosing whether to involve PPC Web Promoting as an advertising device to advance their product(s) and administrations.
I’m not the slightest bit saying that the Web Showcasing devices referenced in this article are bad instruments nor unseemly administrations to use for advancing items and administrations, only that to make them advantageous a private company should have an enormous advertising financial plan set up to be serious at this showcasing approach. There are different methodologies that a business with a little advertising financial plan can utilize to spread the word and grow a client base that is more expense proficient than Pay-Per-Snap Web advertising, and obviously, the items and administrations that a business is elevating closely relates to drawing in clients and deals. Best of luck.
...Why You Should Consider Having Dell Server for Your Needs
Nowadays, most organizations are relying upon computer systems in carrying on with work exchanges. Various computers are being utilized as well as different software applications and as a result of it, keeping the server refreshed and very much kept up with is significant for smooth business tasks. Typically, it is the network overseer who is doing server support occupations. With appropriate arrangement, the applications that are being utilized in your association will run as they are supposed to. Incomplete or absolute network disappointment can be forestalled. You do not believe your business should encounter serious misfortunes, without a doubt! As a term, server is in fact used to portray a container, which holds the processor of the computer, hard drive and memory. Intended to give most extreme figuring power utilizing least space, various servers are typically introduced by associations to help processing power reachable to support various systems, applications and databases.

Legitimate server protecting necessitates a specialist network overseer to perform standard preventive upkeep, including a survey of any conceivable security gambles, customary backup conventions and the general exhibition of the server. As a component of keeping the server looking great, a network head ought to verify that inbuilt system exam utilities are suitably designed and appropriately introduced. To keep the computer network of your business in solid and ideal condition, you ought to consider having customary server refreshes, patches establishment and diagnostics. You want a possible server support intend to expand your business programs and equipment’s possibility serving your company for a really long time. While you have a thought at the top of the priority list what should go into your arrangement, it could be much useful to get server specialists to do the expected upkeep. Through standard backup of data, running diagnostics and fix establishments, your server will be at its maximized operation and subsequently, lessening any mistake and dangers for system disappointments.
Having an effective server upkeep plan intended for you can be the main piece of your business. Each association has may chu hp proliant needs and objectives. Close by the making of a particular arrangement, it is basic to consider exactly how frequently you wish to have server checkup and support performed for your business. With a strong server shielding plan, you can accomplish a reasonable schedule for execution, forestalling delayed business free times. The significance of a sound server fix and support plan cannot be overemphasized. Without it, your business cannot simply arrive at the apex of achievement. Cut off support however can be so expensive on the off chance that you wish to keep network heads within the premises of your business. Be that as it may, you can manage down the expense by reevaluating or getting an IT counseling firm to accomplish the work for you.
...Wonderful Features of WhatsApp GB PRO – You Need To Know
In this particular technical era, WhatsApp gb messenger doesn’t call for any release. An enormous success on this go across-system messenger can be determined from this simple fact; it includes 1 billion dollars lively customers across the world. So, to support this achievement and for your amusement, this impressive messenger routinely becomes updated with some newest functions. Nowadays, WhatsApp gb is rolled out with a few new and different changes that make your connection interesting and straightforward. Many companies and agencies used WhatsApp gb as marketing and advertising computer software to speak making use of their prospective customers. This is because of its simple to use features. Therefore, have a look at these stunning attributes of this auspicious messenger. Go to the WhatsApp gb conversation, tap and carry it for quite a while, a appear menu will appear in front of you. Find the info solution, there you will notice the exact reputation of your message like go through, provided, directed and more. This characteristic is best for both private talks and also group of people chats.

It is amongst the essential attributes of WhatsApp gb. By way of this characteristic, you can quicken your reply time. In this, automatic replies key phrases happened in your screen, for your convenience. You must just kind the Key phrases along with the system instantly reacted with relevant words of it. Protected Your Information: – Normally, everyone would like to protect certain information about their selves from other people. This safety is likewise added in WhatsApp gb functions. Just for this, you will need to click on options, next privacy and then fine-tune your Previous Seen, User profile Image and Position, as outlined by your requirements. You are able to choose possibly everybody, or only you’re Associates, or no person option, according to you wants.
Now, you can even reduce your phone bills, as WhatsApp gb extra a new attribute of Voice Phone calls inside it. A tab possessing phone icon will show up on your whatsapp gb pro display with Talks and Relationships. Via this feature, you can easily make sound calls for the person, as long as he also making use of the newest version of WhatsApp gb. There some chats and video lessons, that contain are specific for you. Therefore, a characteristic of back up is provided for you to store chats, pictures and even video tutorials also. For this, select environment solution, then Talks and Calls, and burst into Chitchat Back up. An alternative of Car Back-up is additionally readily available for your interest.
...Putting a Focal point On 4 of the Best VPN Service Suppliers
There are in a real sense several justifications for why you ought to utilize virtual private networking (VPN). A portion of the advantages include:
- Capacity to conceal your web action from your ISP
- If utilizing a public Wi-Fi, have the capacity of shielding yourself from programmers
While there are numerous VPN service suppliers on the lookout, not all will give you enough service. Here are the absolute best suppliers that you ought to consider:
Express VPN
It has been casted a ballot by a large number of individuals as the best VPN service. This is because of the extraordinary elements that it accompanies. It has servers in more than 78 nations all over the planet. This guarantees that the paces are first class subsequently you can transfer and download your #1 recording quick. The VPN programming is viable with many working frameworks including: Macintosh, is, android, windows and Linux. You just have to download the application that is viable with your gadget. Dissimilar to other service suppliers, Express VPN doesn’t keep utilization logs; hence, you don’t need to stress of your private data getting compromised. The service supplier’s service plans accompany limitless data transfer capacity. This wipes out the concern of raising a ruckus around town cap.

Conceal my butt
Show to a UK organization, the product utilizes OpenVPN. One of its most appealing highlights is exploring interface is simple. This causes it ideal for clients that to have never utilized VPN services. It’s viable with a great many working frameworks. Whether utilizing Android or Windows gadget you will get an application viable with your gadget. The service supplier prides itself of having a specialized help group that will assist you with each question that you have.
IPVanish
It’s controlled by a US organization and one of its extraordinary elements is its basic and direct connection point. This makes the product ideal for the beginner client. Correspondingly to Communicate VPN, its service plans accompany limitless transfer speed. It’s likewise viable with various gadgets including: Linux frameworks, Macintosh, Windows and Android. One of the significant imperfections is that it’s incongruent with the iOS working framework.
Solid VPN
Solid VPN has been in presence starting around 1994 and has numerous alluring highlights. One of the highlights is that it has more than 383 servers in this way furnishing you with quick association speeds. Its service plans don’t have transfer speed limits; along these lines, you don’t need to stress of arriving at your month to month cap. To make it simple to arrive at the client assistance work area, the service supplier has planned numerous stages that you can utilize. You can utilize live visit, email or even call. The client delegates are accessible day in and day out; accordingly, you can get help any season of day or night and learn this here now https://rubyvpn.com/.
...How to Get Your Information from Viruses and Digital Hoodlums during Voyaging?

Travelers are tied in with having a great time and pleasure with loved ones however the present working situation requests you to remain associated every minute of every day. Consequently, whether it is mobile, PC, palmtop or some other gadget; we want to convey our stuff so we ought to stay associated with everybody through any area of the planet. However, this benefit has additionally welcomed a great difficult situation as digital wrongdoings, programmers and viruses that can abuse with our data in any event, when we are voyaging and show numerous aftermaths of it. There are many possibilities checking sends, getting to banks and web-based media records and keeping your children occupied in diversion and internet games during voyaging. Be that as it may, as the vast majority of different explorers who have almost no chance to consider the fringe concerns connected with carrying on with the advanced life, are your contraptions gotten from viruses, information misfortune and different sorts of dangers Are your instruments are furnished with the required antivirus programming yet have you forgotten to totally get them from malwares
Here are a portion of the fundamental tips you want to follow while voyaging so you can remain safe with the best virus assurance programming anytime of time at any objective
- Back up your information this will guarantee that you can recover your information whenever regardless of whether you are mobile or PC is lost or taken.
- Introduce best antivirus programming on your framework since mobile malware is on the climb, it is profoundly fundamental to get antivirus assurance for your mobile and different gadgets. Introducing safely can furnish antivirus and antispyware insurance alongside the other security includes the whole way across your gadgets like workstations, advanced cells, tablets and so forth
- Secure your gadget with solid passwords-assuming your gadgets are gotten with solid passwords an outsider cannot get to your record or data in the event that it is lost or taken. The cyber security news secret phrase ought to be different all of the time for some records and should be a combination of irregular series of numbers, letters in order and images. Continuously reinforce the security of online passwords particularly for banking destinations.
- Switch off record sharing when you are headed for keep programmers from taking touchy information from your PC.
- Impair programmed associations from your workstations. This will keep your PC from programmed association from any remote organizations to your reach.
- While mobile counts on the streets, make a point to download your bank’s true application with the goal that you may not open any copycat website and try not to save your login accreditations.
Network computers: The Vigorous Specialists
With net book computers close by, occupied individuals these days can take care of business regardless of where they are. They could be on a work excursion or a get-away but, they keep on keeping in contact with their representatives…With net book computers nearby, bustling individuals these days can take care of business regardless of where they are. They could be on an excursion for work or a get-away but, they keep on keeping in contact with their representatives and customers. With net book computers, he can settle on a decision, send email and convey reports or talks. In reality, there is no restriction to how one can manage the enthusiastic friends that he has, the net book computers.Netbook computers are more modest and less lumbering contrasted with work areas, which one can only with significant effort bring anyplace. It is as yet more modest than a laptop yet may have comparative capacities and applications. A few great net book computers are currently shown at the site of Indirect web shop. These net book computers are largely helpful, strong and advantageous to utilize.

Indirect brings a few net book computers to the table. There are a few models of the Drove net book and laptop currently introduced and which can be seen from the site. The Drove Net book Laptop Intel N455 has astonishing highlights, a delightful plan, an advantageous regular console and HDD security for data. It is entirely reasonable and it generally works regardless of whether an individual is voyaging. He can take it out anyplace there is Wife sign and begin working. He can begin his laptop and really look at his messages, send an email or simply peruse the web. Understudies will likewise find net book computers valuable. They can utilize them to do their exploration. A few educators these days post the tasks on the web and understudies can accomplish the work and submit online as well. There are additionally books and activities that understudies can without much of a stretch download from their laptops. Driven Net book is outfitted with a huge 12.1″ show that permits clients to effortlessly see archives and Pages.
One more excellent brand of net book computers found on Indirect web shop is the 11.6in Scratch pad. This tablet net book is more modest than other net book computers showed however it has the speed that can stay aware of occupied ways of life. It is exceptionally simple to bring along and doesn’t consume my space when opened. This is helpful for financial specialists and understudies who need net book computers for their day by day assignments. By utilizing this gadget, they can ride the net, send messages, study, form records or do different things. This small net book can work as effectively as net book computers. With this new book , click here no time is squandered regardless of whether one is voyaging or having a get-away. Buying these net book little laptop with be an astute choice for money managers and understudies the same.
...What You Should Know About A Website Wireframe
The website is turning into the best showcasing and publicizing instrument. Be that as it may, sadly, many individuals do not have the foggiest idea about the right ideas and strategy to be applied to take advantage of a site prompting corrupting of the presentation and market esteem. Consequently we have thought of tips that will assist you with picking a decent designer. First of all, when searching for a decent designer it is significant that you request past wireframing work done by the organization. Have various organizations that you would consider to work for yourself and with every one of them take a gander at what they have chipped away at. On a similar note you might need to ask about the different wireframe processes and the time it might take to finish the work. Also, make requests about the expense of the wireframing administrations. See whether any modifications in the process will influence the expenses of the administrations and assuming the organization will offer any limits.
This is to check whether or not an organization is beneficial for you. Wireframing should be refreshed routinely and hence discover additionally on what it will cost you to have the updates. Guarantee that what you should pay for is actually what you need for your site. The following thing to consider is the kind of website streamlining look. Tell the organization your ideal goals of wireframing your site. In case the organization does not appear to get them, it implies that conveyance will be in opposition to your goals and subsequently employing such an organization will be an exercise in futility and assets. Anticipate that the designer should get some information about your site’s objective clients just as its objectives. You ought to be in the situation to figure out what your designated clients needs are and how you might want to convey those necessities. All things considered, a decent designer ought to have the option to construct a utilitarian site that is not difficult to use for both existing and new clients.
Something different that an individual ought to think about when attempting to observe the best designers is the way long it will take them to wrap up the task. Getting your own website going is consistently something extraordinary to do, however an individual regularly just has a restricted measure of time to get the webpage up before your space will lapse. Then, at that point, you need to re-register your area. In this way, an individual has to realize what amount of time the organization will require to get your site designed and dispatched then you will realize how long an individual will have a functioning site up prior to expecting to recharge your enlistment. This coding is the coding languages that an individual likely does not see, yet is vital to the facilitating organization. Dispatching your very own website can be something magnificent. The following stage that you really want to do will be observing wireframe to assist you with getting the site appearing as though what you need.
...